NodeZero TripwiresTM
Delivering a novel and strategic approach to threat detection and automated deception technology
- Rapidly respond to indicators of active threats in high-risk areas of your environment
- Automatically deploy deception technology in proven attack paths for maximum effect
- Integrate malicious activity alerts into your existing threat detection and response workflows
Attackers weaponize new exploits within minutes of their release.
Every minute that an attacker lurks undetected in your network increases your risk.
Strategic Alert Placement
With the NodeZero Tripwires product, NodeZero strategically deploys decoys – such as fake files and fake credentials – along proven attack paths in your environment during autonomous pentests. This ensures that the tripwires are placed where it matters most to your organization.
Contrast this with other deception solutions where you have to decide where to place the decoys. Even the automated ones demand significant setup time and management. These approaches result in intrusive false-positives and alert fatigue for security teams.
Key Features

Automated Deployment
Seamlessly integrated with NodeZero’s autonomous pentesting, tripwires are automatically deployed in high-risk areas without the need for manual intervention.

Real-Time Alerts
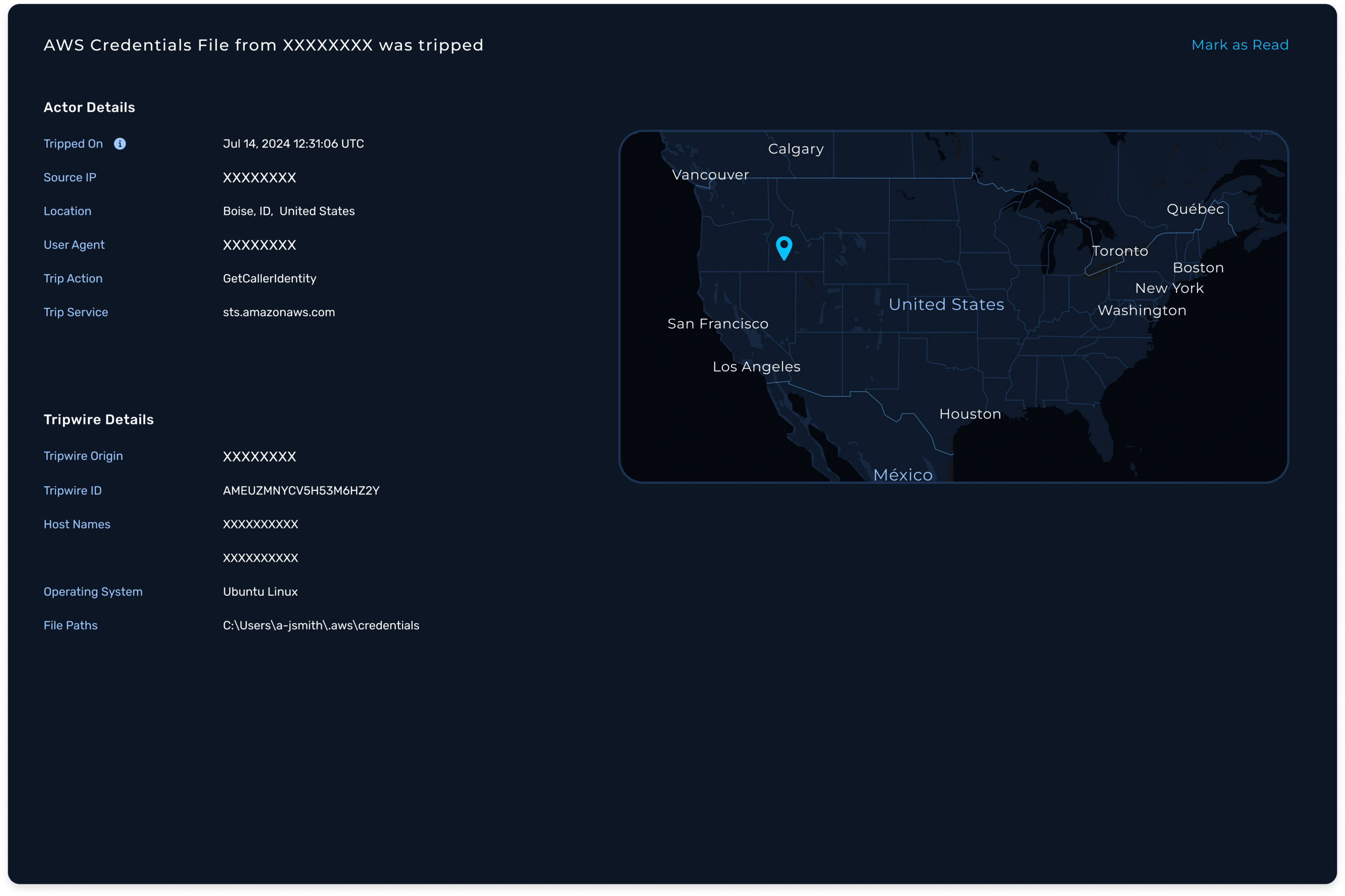
Receive immediate alerts in the NodeZero Tripwires notification center, with detailed information on the nature of the access attempt, location, and potential threat to help investigations.

Low False-Positive Rate
High-quality signal ensures that alerts are meaningful and actionable, minimizing the occurrence of false positives.

Versatile Tripwire Types
Deploy a variety of tripwires to detect unauthorized access attempts across different attack vectors. Types include AWS API Key, mysqldump, and Windows Suspicious Process Monitor.

Easy-to-Use Management Console
Centralized dashboard for managing all deployed tripwires and viewing alert histories. Simple notification controls.

Integration with Security Tools
Easily integrate tripwires with existing SIEMs and other security tools into your existing incident response workflows.
Activate with One Click
As NodeZero maneuvers autonomously through your environment, it automatically deploys tripwires in assets that are likely to be attacked:

Start a Pentest
Select the Tripwires option when initiating any internal, external, Phishing Impact, or Rapid Response pentest to give NodeZero permission to drop tripwires during the test.

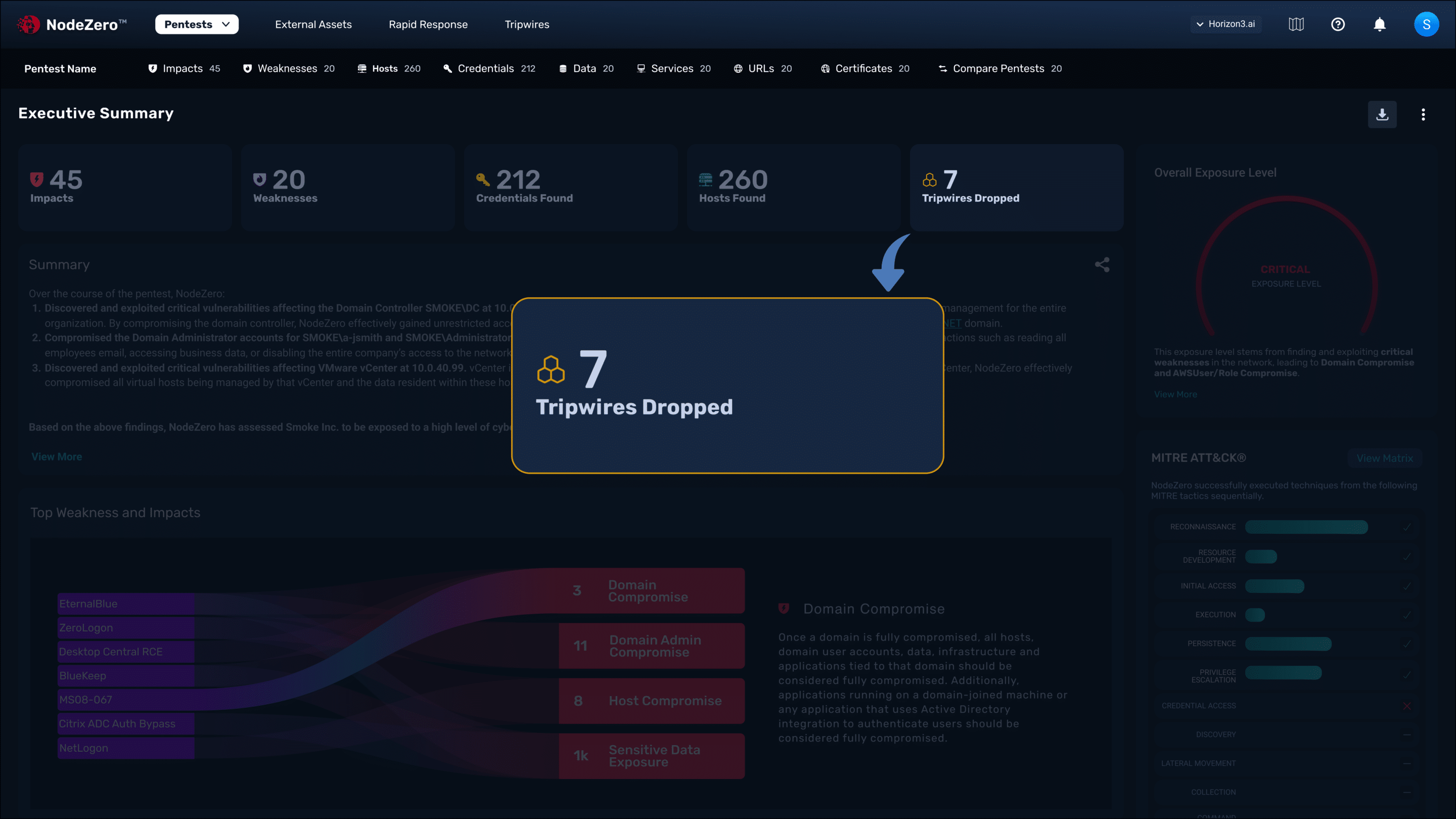
Tripwires Dropped Automatically
During the test, NodeZero deploys appropriate tripwire types along proven attack paths in assets revealed to be exploitable.

Tripwires Dropped Automatically
During the test, NodeZero deploys appropriate tripwire types along proven attack paths in assets revealed to be exploitable.
Add a Layer of Protection for Your Most Critical Assets


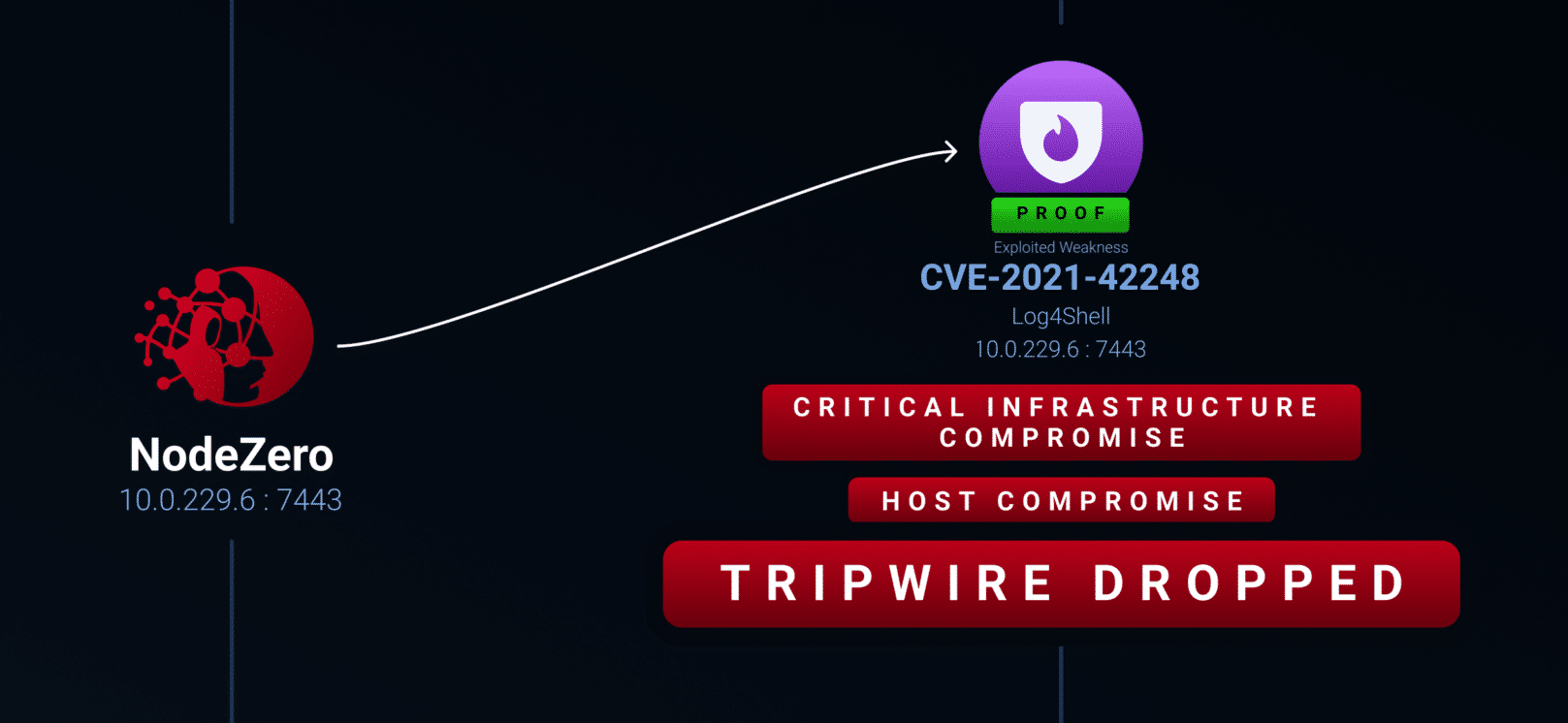
Detect Attacker Exploitation of N-Day Threats
Protect your organization in the time critical window between the identification of an emerging threat and the availability of a security update.
Example: During a Rapid Response pentest, NodeZero identifies a host that can be compromised with the new vulnerability. NodeZero immediately alerts you that your organization is impacted by this threat and simultaneously deploys a tripwire to the location. Even before the pentest is complete, your team is alerted when a threat actor attempts to run a process indicative of malicious intent.
The early warning delivered with relevant details allows you to escalate the appropriate response in that critical early time window that attackers are primed to exploit.
Detect Credential Compromise in Internal Pentests
Use Tripwires to detect credential compromise across your entire digital infrastructure.
Example: After gaining domain admin access in an internal pentest, NodeZero pivoted to Azure Entra ID and compromised the account of the Azure global admin. During the test, NodeZero strategically placed Windows Suspicious Process Monitor and Azure Login Certificate tripwires on the domain admin, the Azure Entra ID global admin's machines, and other key hosts containing sensitive data.
NodeZero alerts the team when a threat actor attempts to use the Azure credential tripwire or run a tripwired process.
Augment Your Phishing Simulations
Expand the benefit of the Phishing Impact test by using Tripwires to detect whether phishing-prone credentials have been compromised.
Example: During a Phishing Impact test, NodeZero harvests phishing-prone credentials with admin privileges. It uses the credentials to deploy tripwires to a network share, dropping Azure login keys across multiple user directories to detect and alert you to malicious activity.
Ready to connect with Horizon3.ai?
Submit the form below.